Strengthen Your Security Today
Take control of your vulnerability management process with Carson & SAINT’s proactive and tailored solutions. Contact us today to enhance your security posture with a comprehensive, effective vulnerability management program.
Protect Your Business with Customized Cyber Security Assessment Services
Keeping your business secure from cyber threats requires a thorough, customized approach. Every business is unique, which means your security needs are, too. That’s why our Security Assessment Services are specifically crafted based on your organization’s infrastructure, risks, and goals.
Whether you’re concerned about data breaches, insider threats, or compliance requirements, we’ll work with you to identify and address vulnerabilities to strengthen your security posture. Our goal? To ensure you have the protection you need without compromising your business’s ability to grow and innovate.
What Is a Security Assessment?
A cyber security assessment is a structured evaluation of your IT infrastructure, applications, and processes to identify existing and potential vulnerabilities. Carson & SAINT’s assessment services deliver clear, actionable recommendations to help you secure your business against ever-evolving threats.
Here’s how a security assessment can benefit you:
Identify Weak Points
We pinpoint areas where your systems might be at risk, from outdated software to access control gaps.
Evaluate Risk Exposure
We assess how likely these vulnerabilities are to be exploited and the potential impact they could have on your business.
Recommend Solutions
You’ll receive a detailed action plan with steps to address and mitigate risks in a way that fits your operations and budget.
Ensure Compliance
Our services help ensure that organizations in regulated industries, such as healthcare, finance and government, meet standards like HIPAA, PCI DSS and NIST.
Our assessment process provides a clear view of your security posture and a roadmap to address the most significant risks to your business.
Our Cyber Security Assessment Services
Carson & SAINT offers a range of specialized assessments to address the unique challenges in your environment:
Vulnerability Assessment:
Identify security weaknesses in your networks, systems, and applications through comprehensive scanning and reporting, helping you patch and secure vulnerabilities before they can be exploited.
Penetration Testing (Pen Testing):
Simulate real–world cyber attacks to discover exploitable vulnerabilities in your IT infrastructure. We offer various pen testing services, including external, internal, and wireless testing to ensure all attack vectors are covered.
Risk Assessment:
A high–level evaluation that identifies and prioritizes potential risks, helping you focus on the most critical security gaps that could impact your business.
Compliance Assessment:
Ensure that your security measures meet the necessary regulatory standards, such as PCI DSS, HIPAA, or GDPR, avoiding non–compliance penalties and ensuring you protect customer data effectively.
Cloud Security Assessment:
Evaluate the security of your cloud services and infrastructure to protect your organization from threats specific to cloud environments.
Network Security Assessment:
Examine the integrity of your internal and external network configurations to uncover vulnerabilities in firewalls, routers, and other network components.
Application Security Assessment:
Review and analyze your web, mobile, and desktop applications for security flaws like SQL injection, cross–site scripting (XSS), and insecure authentication methods.
Social Engineering Assessment:
Test your employees’ awareness of social engineering attacks like phishing, baiting, and impersonation, ensuring your team is prepared for human–based threats.
Wireless Security Assessment:
Protect your organization from vulnerabilities in wireless networks by assessing configurations, access points, and encryption methods to ensure secure connectivity.
Physical Security Assessment:
Review the physical access controls of your offices, data centers, or other facilities to prevent unauthorized access and safeguard sensitive areas from physical threats.
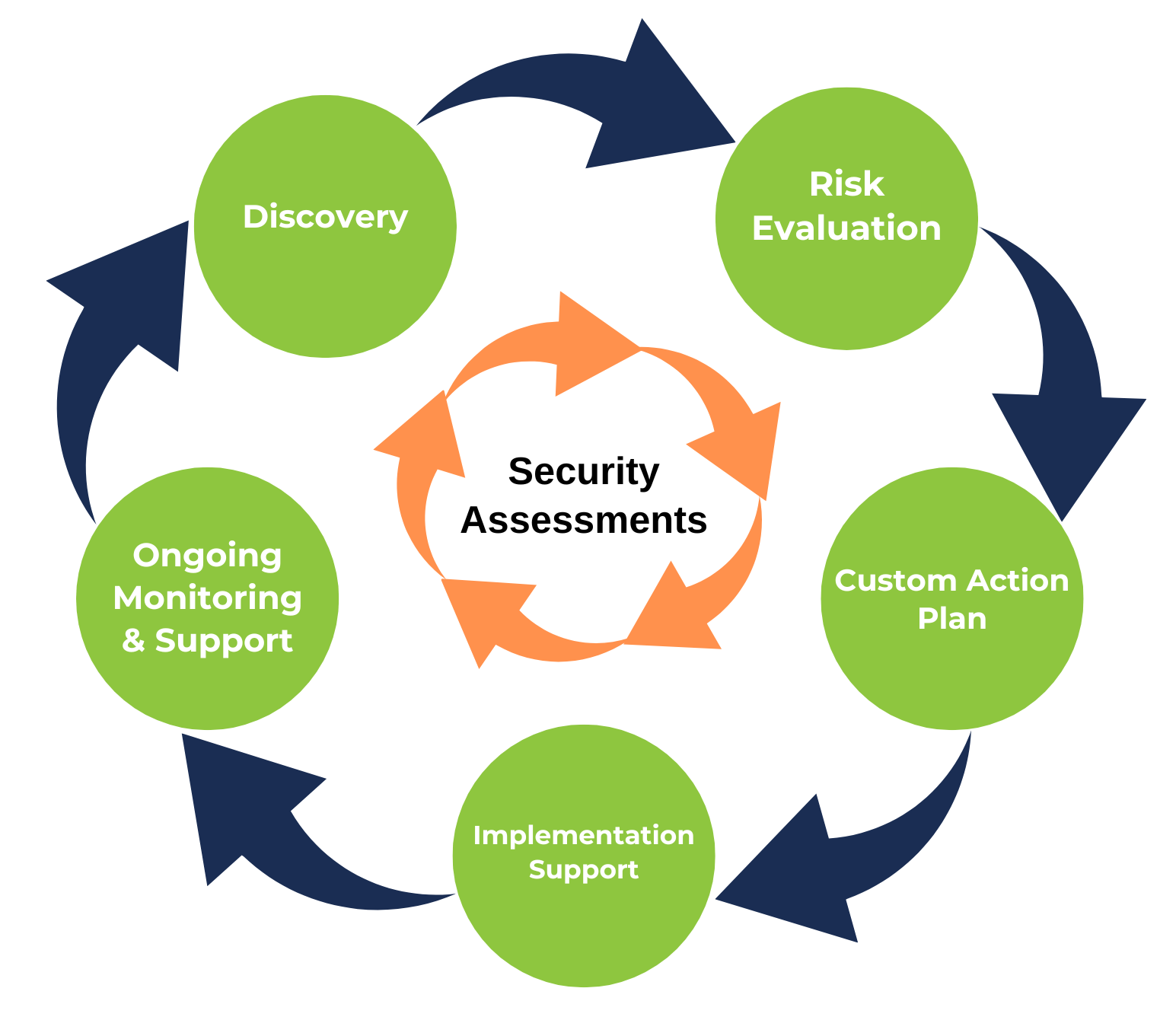
Our Approach to Cyber Security Assessments
Effective security assessments require an approach that reflects the specific needs and risks of each business. Carson & SAINT begins every cyber security assessment with a deep understanding of the organization’s unique environment, risks, and goals. Here’s our five–step process:
1. Discovery
We start by conducting a thorough review of your systems, policies, and procedures. This includes evaluating your IT infrastructure, applications, access controls, and any third–party integrations that could pose a risk.
2. Risk Evaluation
Our team analyzes the findings to identify potential vulnerabilities and assess their risk level. We’ll prioritize these risks based on how likely they are to be exploited and the impact they could have on your business.
3. Custom Action Plan
Once the risks are identified, we provide you with a customized roadmap of solutions. Whether it’s upgrading security protocols, tightening access controls, or enhancing your firewall, we’ll help you find cost–effective solutions to mitigate each risk.
4. Implementation Support
We don’t just leave you with a report. Our team is available to help implement the recommended solutions, ensuring that your security enhancements are applied efficiently and effectively.
5. Ongoing Monitoring & Support
Your security needs will evolve as your business grows and new threats emerge. We offer ongoing monitoring and support services to ensure your systems remain secure over time.
Why Choose Us for Cyber Security Assessment Services?
Carson & SAINT’s team is deeply experiences in cyber security and has been instrument in setting industry standards. We know security is about protecting the integrity of your organization, your customers, and your reputation. When you choose us, you’re choosing a partner who is as invested in your success as you are.
Here’s why businesses trust us:
Tailored Assessments:
We start by conducting a thorough review of your systems, policies, and procedures. This includes evaluating your IT infrastructure, applications, access controls, and any third–party integrations that could pose a risk.
Expertise Across Industries:
With years of experience in industries ranging from healthcare to finance and government, we understand the unique challenges your organization faces and provide security strategies that work in your environment.
Actionable Recommendations:
You won’t get a laundry list of technical jargon. Instead, you’ll receive clear, actionable steps to improve your security posture in a way that fits your operations and budget.
Compliance-Focused:
Whether you need to meet industry standards like PCI DSS or NIST, we’ll ensure your assessment aligns with your compliance requirements, helping you avoid fines and maintain trust with your customers.
Long-Term Partnership:
Security is not a one–time effort. We’re here to provide ongoing support and monitoring to keep your systems secure in the face of new and evolving threats.


The Benefits of a Cyber Security Assessment
Investing in a cyber security assessment strengthens your business’ ability to manage risk and maintain resilience. Key benefits include:
Proactive Risk Management:
Identify and address potential threats before they can cause harm, minimizing the chances of a costly breach or attack.
Improved Compliance:
Stay up–to–date with industry regulations and avoid the fines, penalties, and reputational damage that come with non–compliance.
Enhanced Business Continuity:
By understanding your vulnerabilities, you can take steps to ensure your systems are resilient, reducing the risk of downtime or data loss.
Informed Decision-Making:
A clearer picture of your security posture allows you to make smarter, more strategic decisions about where to invest your resources.
Let’s Work Together to Protect Your Business
Take the first step toward a more secure future. Your organization’s security is our top priority. Our team of experts is ready to work with you to identify risks, implement solutions, and build a security framework that grows with your business.


