Advanced Analytics
Streamline analysis. Increase ROI.
Setting priorities to achieve better ROI.
Assessing even the smallest environment can result in hundreds, if not thousands of scan results. At an enterprise that scans hundreds of sites, data centers, and cloud instances, results are routinely in the millions for individual assessments. Given the sheer volume of data, and the criticality of finding and resolving exposures, data analysis capabilities must facilitate fast and easy methods of selecting, filtering, analyzing and prioritizing results that provide the highest value in the shortest amount of time.
Within a holistic vulnerability assessment, SAINT Security Suite’s on-premise, cloud, and hybrid solutions provide a common set of tools and features to simplify the complexity of vulnerability assessments and interoperate with a fully integrated assignment and validation to simplify work – thus increasing ROI across your security investment.
Setting priorities to achieve better ROI.

Assessing even the smallest environment can result in hundreds, if not thousands of scan results. At an enterprise that scans hundreds of sites, data centers, and cloud instances, results are routinely in the millions for individual assessments. Given the sheer volume of data, and the criticality of finding and resolving exposures, data analysis capabilities must facilitate fast and easy methods of selecting, filtering, analyzing and prioritizing results that provide the highest value in the shortest amount of time.
Within a holistic vulnerability assessment, SAINT Security Suite’s on-premise, cloud, and hybrid solutions provide a common set of tools and features to simplify the complexity of vulnerability assessments and interoperate with a fully integrated assignment and validation to simplify work – thus increasing ROI across your security investment.
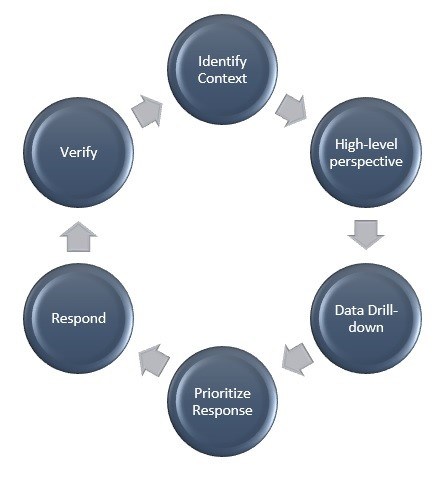
LEVERAGE DATA ANALYTICS FOR SUCCESS
Enable users to identify the context for analysis from one or more types of assessments.
Help find the most important issues to resolve quickly, with the least amount of time and effort possible.
Provide support for both high-level and fact-level details to enable decision-making work prioritization
Perform post-resolution validation to ensure risks and exposures have been resolved.
Identify Context
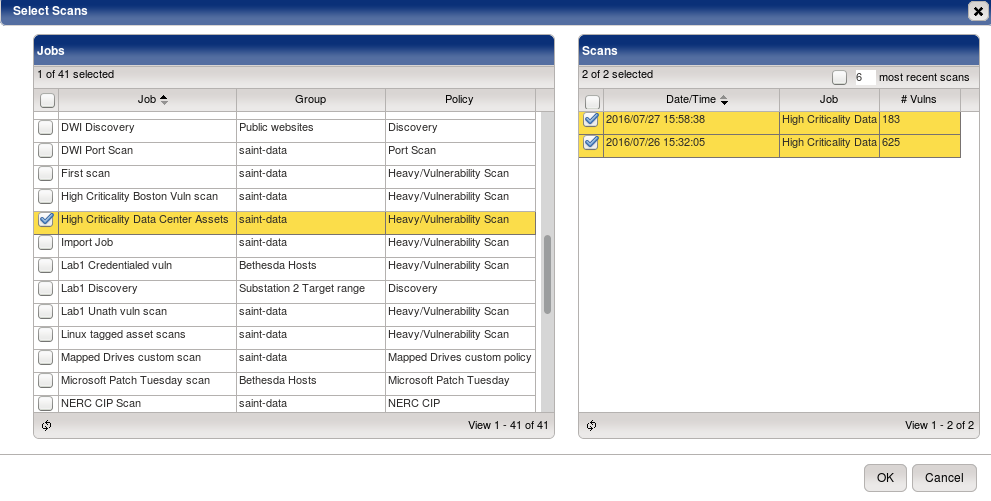
Performing a comprehensive assessment starts with selecting the results of one or more scans, based on the scan policy, time, and asset scope applicable to the investigation. Asset managers, system owners, administrators, and security experts can conduct scans based on numerous types of assessments: comprehensive vulnerability scans, configuration assessments, penetration tests, content scans, and more.
Once scans have been completed they are available for analysis by job. A user can select one or more jobs and/or scans to correlate the combined results, building context for the analysis. For example, you can select the latest vulnerability scan on a data center and the latest PCI scan on an external webserver to view the combined exposures from the two scans. Or you can select one scan before system changes are made and one after to determine whether all risks have been remediated.
Identify Context
Performing a comprehensive assessment starts with selecting the results of one or more scans, based on the scan policy, time, and asset scope applicable to the investigation. Asset managers, system owners, administrators, and security experts can conduct scans based on numerous types of assessments: comprehensive vulnerability scans, configuration assessments, penetration tests, content scans, and more.
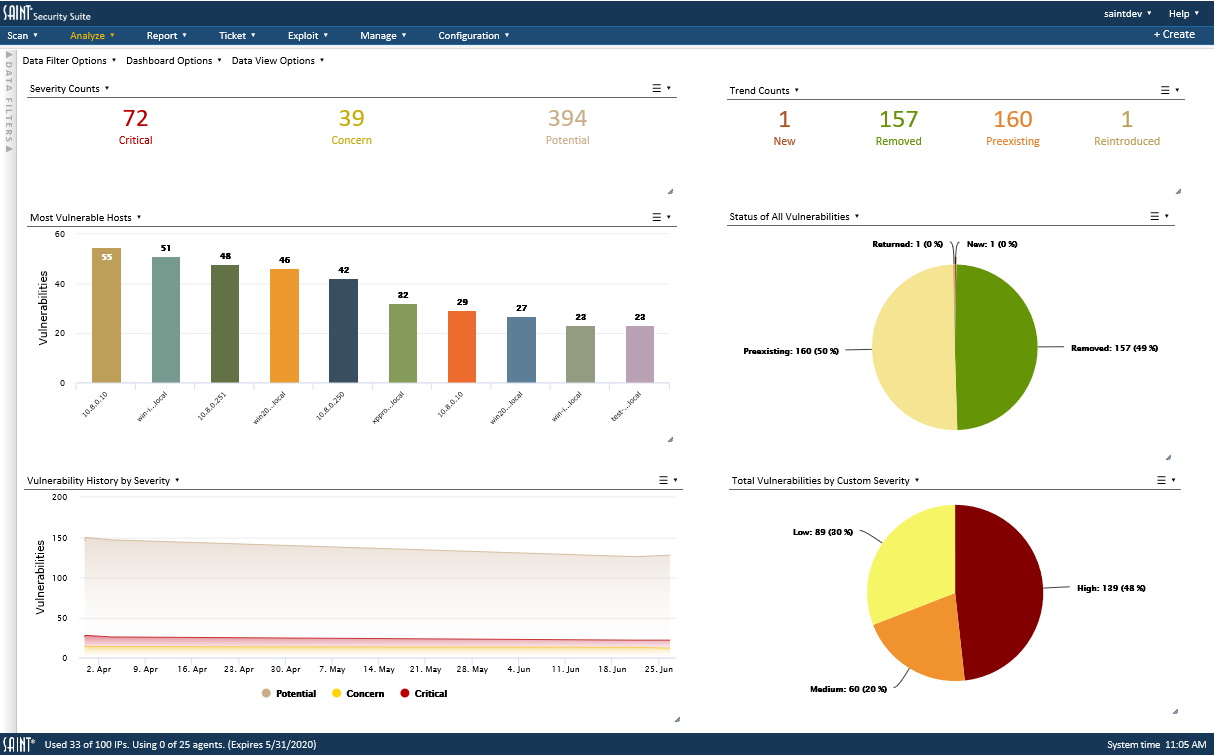
Gain a high-level perspective.
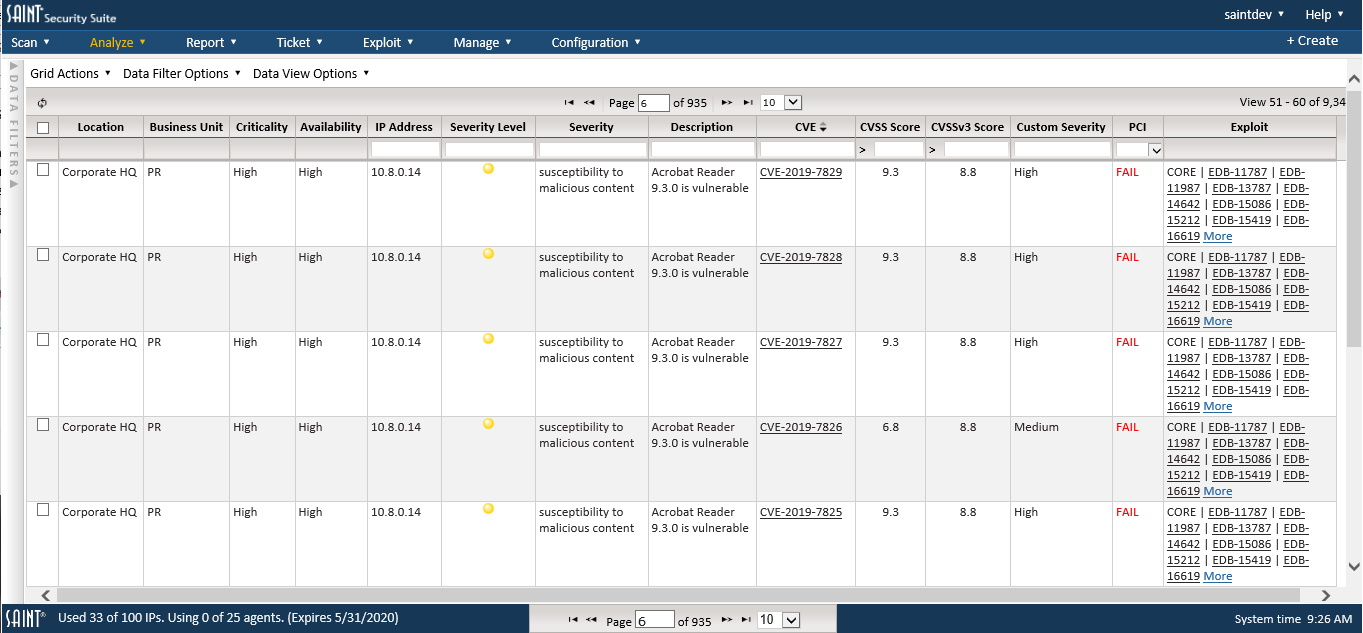
Vulnerability scans can produce a lot of detailed information about each scanned host. This can include basic host information, such as IP address, MAC address, hostname, operating system version, and NetBios as well as potential and known risks related to running services, open ports, patch levels, vulnerable software, operating system configurations, applications, and more.
SAINT analytics can save analysis time by taking this information and correlating key data points into high-level dashboards with summary counts by key metrics and severity scores. It also provides quick data drill-down to underlying issues from these key counts and scores to save time finding the most important exposures.
Gaining a high-level perspective of complex results helps to communicate the overall health of the security program, reveals trends, and helps you visualize top performers, most vulnerable hosts, most frequently found vulnerabilities, and other top concerns.
Using SAINT Security Suite’s asset management capabilities, you can execute assessments based on hosts that support key business operations. You can then analyze the results based on these business perspectives. At a tactical level, analysts can view high-level results – correlated from all of the data in context – to provide a quick perspective on the scope of the issues to be addressed. Simply use point-n-click actions to drill down to the bottom line quickly. There’s no need to dig through thousands of raw results or review pages of reports.

Gain a high-level perspective.

Vulnerability scans can produce a lot of detailed information about each scanned host. This can include basic host information, such as IP address, MAC address, hostname, operating system version, and NetBios as well as potential and known risks related to running services, open ports, patch levels, vulnerable software, operating system configurations, applications, and more.
SAINT analytics can save analysis time by taking this information and correlating key data points into high-level dashboards with summary counts by key metrics and severity scores. It also provides quick data drill-down to underlying issues from these key counts and scores to save time finding the most important exposures.
Gaining a high-level perspective of complex results helps to communicate the overall health of the security program, reveals trends, and helps you visualize top performers, most vulnerable hosts, most frequently found vulnerabilities, and other top concerns.
Using SAINT Security Suite’s asset management capabilities, you can execute assessments based on hosts that support key business operations. You can then analyze the results based on these business perspectives. At a tactical level, analysts can view high-level results – correlated from all of the data in context – to provide a quick perspective on the scope of the issues to be addressed. Simply use point-n-click actions to drill down to the bottom line quickly. There’s no need to dig through thousands of raw results or review pages of reports.