Penetration Testing
Quantify risks. Defend your network.
Remediating your highest risks.
SAINT Security Suite’s penetration testing provides easy-to-use, powerful capabilities to test and verify risk exposures from vulnerabilities in your network.
Based on years of vulnerability and exploitation experience, Carson & SAINT developed the penetration testing capabilities to interoperate with the SAINT Security Suite vulnerability scanner. This allows you to exploit a vulnerability discovered by the scanner to irrefutably confirm its existence.
Advanced users can also add their own exploits, modify existing exploits, and use SAINT Security Suite’s post-exploitation tools to extend value within the vulnerability investigation process. This provides a better return on investment by enabling faster and more effective remediation actions on your highest-risk vulnerabilities.
Remediating your highest risks.
SAINT Security Suite’s penetration testing provides easy-to-use, powerful capabilities to test and verify risk exposures from vulnerabilities in your network.
Based on years of vulnerability and exploitation experience, Carson & SAINT developed the penetration testing capabilities to interoperate with the SAINT Security Suite vulnerability scanner. This allows you to exploit a vulnerability discovered by the scanner to irrefutably confirm its existence.
Advanced users can also add their own exploits, modify existing exploits, and use SAINT Security Suite’s post-exploitation tools to extend value within the vulnerability investigation process. This provides a better return on investment by enabling faster and more effective remediation actions on your highest-risk vulnerabilities.
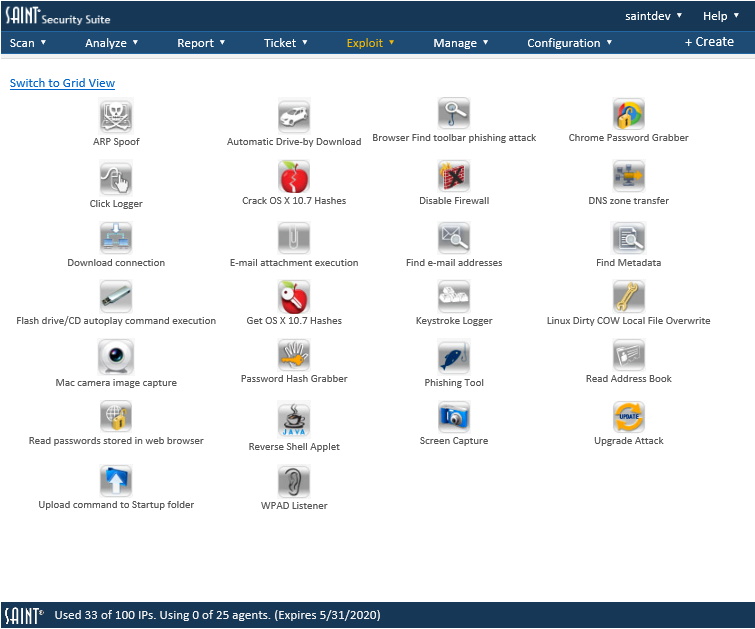
SAINTexploit TOOLS
SAINT Security Suite comes with a collection of exploit tools to help with every step of your penetration test.
Reconnaissance: Finding domain e-mail addresses
Social engineering: Phishing
Penetration evidence gathering: Keystroke loggers
GAIN POWERFUL CAPABILITIES
Go beyond simply detecting vulnerabilities to safely exploiting them.
Demonstrate the path an attacker could use to breach your network.
Quantify risk to the system.
Manage resources more efficiently to better defend information assets.
SAINTexploit at a Glance
- Exploits vulnerabilities found by the SAINT scanner.
- Proves the existence of critical vulnerabilities.
- Includes IPv4 and IPv6 exploits.
- Features exploit tunneling that allows you to run penetration tests from an exploited target.
- Features seamless integration with the SAINT Security Suite GUI.
- Boasts an extensive, multi-platform exploit library.
- Includes remote, local, and client exploits.
- Includes application, SQL, XSS, and PHP exploits.
- Provides automatic penetration testing.
- Runs individual exploits on demand.
- Includes website emulator and email forgery tool with built-in design templates.
Gain new levels of visibility.
The penetration testing tool exploits vulnerabilities to give you insight into how your system and network security would fare against attackers.
Quantify risk.
Determine the level of risk to your information assets by running controlled exploits on your system. Generate reports to better understand the true weaknesses in your network. By demonstrating the path an attacker could use to penetrate your network, you can estimate the potential damage to your data.
Manage resources more efficiently.
By proving the existence of vulnerabilities, you can focus attention and resources where they are needed most. Knowing with confidence the extent of your network vulnerability allows you to manage remediation efficiently.
Defend your network better.
Armed with evidence of system weaknesses, you’re better equipped to fix vulnerabilities and secure the network. The tool provides recommendations to enable vulnerability resolution at the end of each session.
Work efficiently.
Manage penetration testing in-house with a browser-based user interface. It offers seamless integration with vulnerability scanning and analysis features and additional tools to test client vulnerabilities such as Web browsers, databases, and desktop applications.
Stay ahead with continuously updated exploits.
SAINT Security Suite provides an extensive, multi-platform, exploit library that provides up-to-the-minute information on the latest posted vulnerabilities. Pre-designed penetration testing policies use all available exploits for any given operating system or software type from this library to ensure current and previously scheduled penetration tests automatically assess based on all available exploits without manual intervention.