Vulnerability Management
Discover risk. Remediate urgently.
Finding weaknesses before they become exploits.
As a vulnerability management solution, SAINT Security Suite’s security research and development efforts focus on investigation, triage, prioritization, and coverage of vulnerabilities of the highest levels of severity and importance. Not willing to settle for just blanket coverage and raw data, our analysts focus on developing tools for what matters to our customers, while working to reduce content that is less relevant or less valuable for risk analysis, remediation, and continuous monitoring. In this capacity, Carson & SAINT develops custom tutorials that describe the background, problem, related vendor, and industry references, as well as detailed remediation guidance.

A malicious data breach can destroy your business!
Even Small to Mid-Sized Companies must protect against data breaches -with damages averaging $3.6 million per cyber attack globally. Check out our whitepaper to learn more.
60 percent of small companies go out of business within six months of falling victim to a data breach or cyber attack. With both the financial security and future of your business on the line, it’s crucial for organizations of all sizes to have measures in place to monitor suspicious network activity.
Finding weaknesses before they become exploits.

As a vulnerability management solution, SAINT Security Suite’s security research and development efforts focus on investigation, triage, prioritization, and coverage of vulnerabilities of the highest levels of severity and importance. Not willing to settle for just blanket coverage and raw data, our analysts focus on developing tools for what matters to our customers, while working to reduce content that is less relevant or less valuable for risk analysis, remediation, and continuous monitoring. In this capacity, Carson & SAINT develops custom tutorials that describe the background, problem, related vendor, and industry references, as well as detailed remediation guidance.
STEP 1
IDENTIFY
VULNERABILITY MANAGEMENT
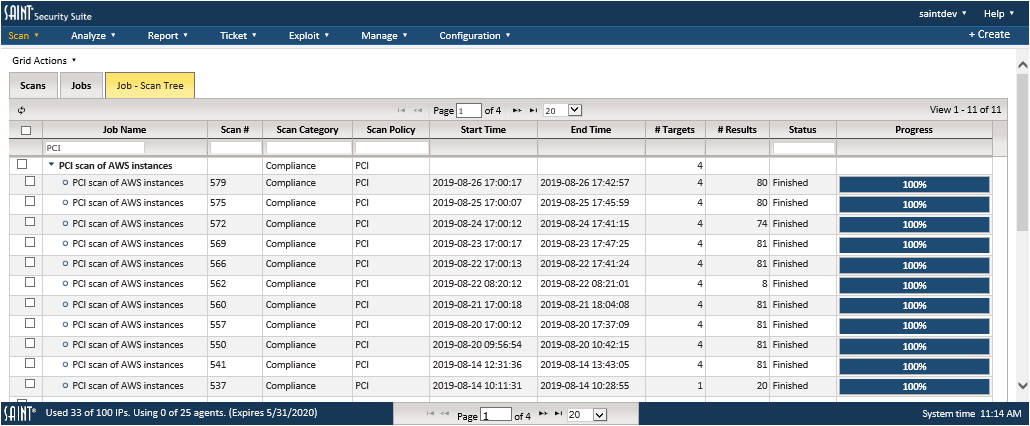
Scan Job Tree View: SAINT Security Suite makes managing your recurring scan jobs easy with an expandable job-scan tree and paged grids that are fully searchable and sortable.
STEP 2
ASSESS
- Operating system and software vulnerabilities
- Patch deficiencies
- Microsoft Patch Tuesday assessments
- Web application vulnerabilities and risk exposures
- State of anti-virus installations
- Configuration assessments based on industry-standard best-practices
- Sensitive content exposure
- Operating system and software vulnerabilities
- Patch deficiencies
- Microsoft Patch Tuesday assessments
- Web application vulnerabilities and risk exposures
- State of anti-virus installations
- Configuration assessments based on industry-standard best-practices
- Sensitive content exposure
These are just a few examples of the types of risk exposures identified by SAINT Security Suite. We are continuing our research and coverage into new and evolving risks in technologies such as mobile, medical devices, embedded firmware, and the Internet of Things (IoT) to ensure our solutions evolve as technologies and threats evolve.
STEP 3
REMEDIATE
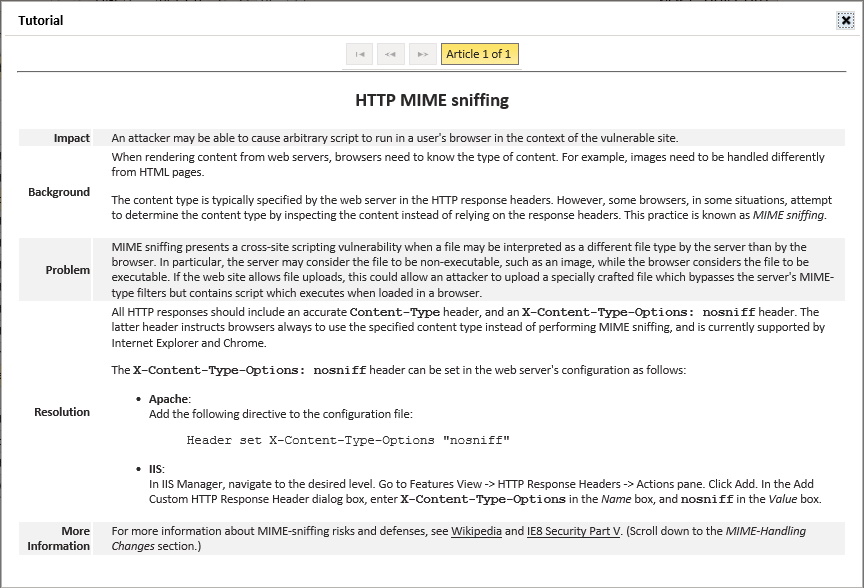
Fast, effective response to critical exposures is fundamental to risk management. SAINT Security Suite provides instructional remediation tutorials, rules-based ticketing for response tracking, and automated workflows to auto-close tickets once remediation has been validated. Using SAINT assessment and tracking workflow increase ROI by decreasing the time spent digging through content, and security teams to prioritize remediation activities that focus efforts on the greatest risks to the business.
SAINT Security Suite also provides interoperability and integration with several SIEM, incident response, asset management, and GRC solutions. This supports data correlation, quarantine actions, and incident-response measures within a more holistic risk-management solution that includes a comprehensive suite of technologies.
STEP 4
VALIDATE
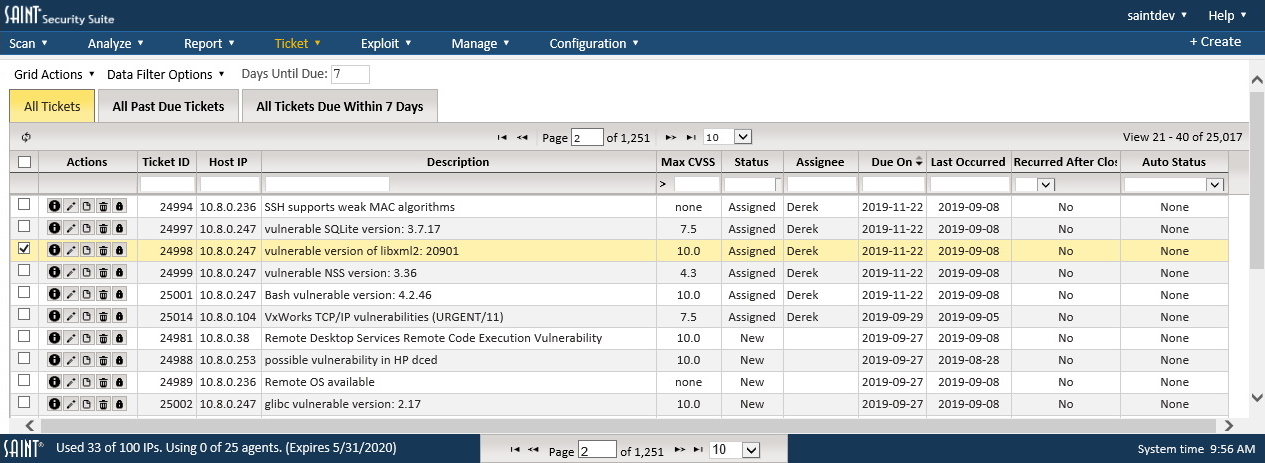
Performing frequent vulnerability scanning and assessment activities is not enough. You must conduct continuous monitoring, assessment, and remediation of known risks and exposures and follow up with validation processes to ensure remediation actions have been completed and risks remain low. Scheduling recurring scans within defined, time-based scanning windows can ensure reassessments and validation are conducted within the context of approved procedures while identifying new, pre-existing or reintroduced vulnerabilities that need to be addressed.